About Threat Watch
Threat Watch is your mobile-first command center for cybersecurity health. Designed for modern IT teams, security professionals, and business leaders, this unified intelligence platform delivers a clear, actionable picture of your organization's digital risk posture directly to your phone or tablet. It goes beyond traditional monitoring by actively analyzing your assets, vulnerabilities, and exposures across multiple critical fronts. The app-centric experience provides real-time insights and automated assessments, enabling you to move from reactive alerting to proactive risk management. The core value is speed and clarity: identify lurking threats like compromised credentials or dark web exposures, prioritize them based on your unique environment, and execute mitigation strategies faster than ever, all from a single, intuitive dashboard designed for on-the-go security management.
Features of Threat Watch
Comprehensive Cyber Health Dashboard
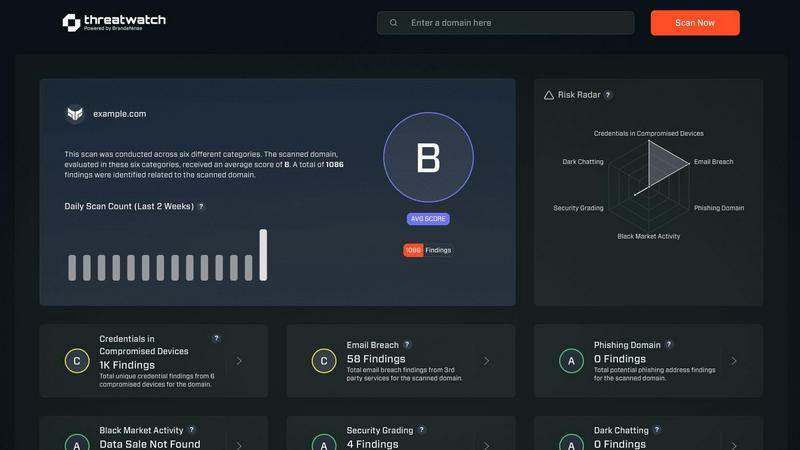
Get an instant, visual overview of your organization's security posture right on your mobile home screen. The dashboard synthesizes data from all monitored categories into a single, easy-to-understand health score, allowing you to gauge overall risk at a glance and drill down into specific issues with a simple tap.
Real-Time Exposure Monitoring
Continuously scan for compromised employee credentials, breached accounts, and phishing addresses linked to your domain. Receive immediate push notifications the moment a new exposure is detected on the dark web or in breach databases, enabling you to act before attackers can exploit the information.
Automated Asset & Vulnerability Assessment
The app automatically discovers and inventories your organization's digital assets and connected devices. It then correlates this data with global vulnerability feeds to highlight unpatched software, misconfigurations, and compromised devices that pose the greatest risk to your network, prioritizing what to fix first.
Dark Web Surveillance Alerts
Proactively monitor underground forums, marketplaces, and chat rooms for mentions of your company's data, intellectual property, or leaked credentials. This feature brings dark web intelligence into a manageable mobile format, alerting you to threats that would otherwise remain invisible.
Use Cases of Threat Watch
Proactive Breach Response for IT Teams
IT administrators use Threat Watch to get ahead of potential breaches. By receiving instant mobile alerts about compromised employee passwords, they can enforce immediate password resets and enable multi-factor authentication before the credentials are used in an attack, significantly reducing the window of opportunity for hackers.
Executive Risk Reporting
Security leaders and executives leverage the app's clean dashboard and health score to quickly report on the organization's cybersecurity status during board meetings or strategic briefings. The mobile-centric reports provide a high-level, real-time view of risk without requiring deep technical dive-ins.
Third-Party Vendor Risk Assessment
Organizations can use Threat Watch to evaluate the security health of their partners and vendors. By monitoring for breaches or exposures associated with vendor domains, companies can identify supply chain risks and initiate crucial conversations about security practices before a joint incident occurs.
Rapid Incident Triage On-The-Go
When a security alert fires from another system, analysts can use Threat Watch on their mobile device to perform rapid triage. They can instantly check if related credentials are already exposed, if the affected asset has known vulnerabilities, or if there's chatter on the dark web, providing critical context from anywhere.
Frequently Asked Questions
How does the free scan work?
The free scan is a quick, non-intrusive assessment that evaluates your publicly available digital footprint. You simply provide your company domain, and Threat Watch scans multiple databases and sources for compromised credentials, phishing sites impersonating your brand, and mentions of your assets on the dark web, delivering a summary report of findings.
What kind of assets does Threat Watch discover?
Threat Watch automatically identifies internet-facing assets like web servers, mail servers, and network devices associated with your domain. It also helps map your digital surface by discovering connected devices and cloud instances that may be exposed, providing a foundational inventory for ongoing security monitoring.
Is the mobile app available for both iOS and Android?
Yes, Threat Watch is built with a mobile-first philosophy and offers dedicated, full-featured applications for both iOS and Android platforms. All core functionalities, including the dashboard, real-time alerts, and health score, are accessible from your smartphone or tablet for true on-the-go security management.
How often are the scans and monitoring updated?
Monitoring is continuous and in real-time. Our systems constantly ingest data from global threat intelligence feeds, breach databases, and dark web sources. Automated asset and vulnerability assessments are run on a configurable schedule, typically daily, to ensure your cyber health score and insights are always based on the latest information.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt is a mobile-first app that creates and signs legally binding contracts in minutes.
aVenture
aVenture is an AI-driven platform for in-depth startup research, competitor mapping, and investor tracking.